Authentication
One of Welshare's main long term design objectives is guaranteed, provable privacy. Hence, a cornerstone of the protocol design is to derive purpose bound accounts from user root keys that differ by application context. This approach improves the privacy of each entity on the protocol: it's impossible for third parties to correlate identifiers with the root accounts (ie users). If you're interested in the technical backgrounds, check out our key derivation docs.
As many other concepts on the Welshare protocol this idea is quite experimental, its implementation not final and the decorrelation guarantees brittle, as we right now use just one derived key for all subsequent operations and that of course is not sufficiently decorrelating user accounts yet.
Logging in / Root Profile Control
Every Welshare user completes a Siwe login process with a keypair that deals as their account root key. They can either use their favorite crypto wallet or create a dedicated embedded (app) wallet that's secured by our partner Privy. Privy's "self-custodial" wallets provide similar security guarantees as non-custodial wallets and they are are recoverable by a social login of your choosing.
User Storage Keys
When starting a data submission, users derive a new secp256k1 keypair using a deterministic EIP-712 signature by their root key and salt values for added entropy. They are asked to do so in the respective dialogs or can manually create (and locally revoke) it on the Welshare wallet app.
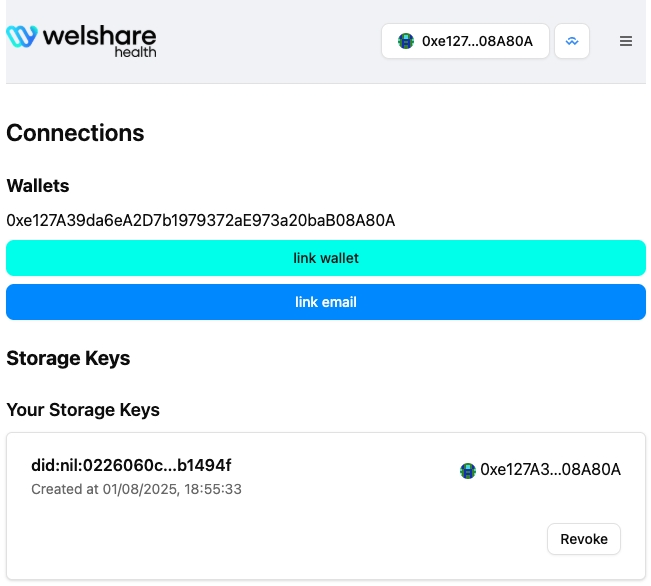
Those keys are stored in local browser storage and are used to sign off secret data transfers. They should by no means be used to control any asset on any chain. Storage keys are used by users to directly interact with Nillion nodes (that's where they got their name from) after Welshare delegated NUCs to them.